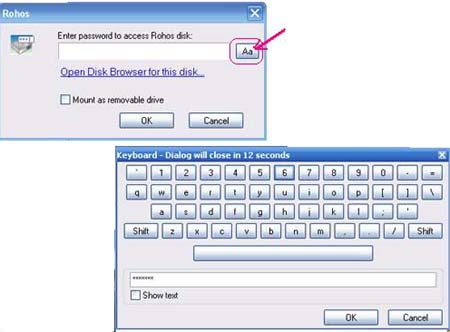
 For greater security and convenience, instead of a password you can use an electronic USB key to decrypt and open a disk. As a key, you can use a USB Flash storage device, a token, or a smart card. A full list of suitable devices can be found here.
For greater security and convenience, instead of a password you can use an electronic USB key to decrypt and open a disk. As a key, you can use a USB Flash storage device, a token, or a smart card. A full list of suitable devices can be found here.
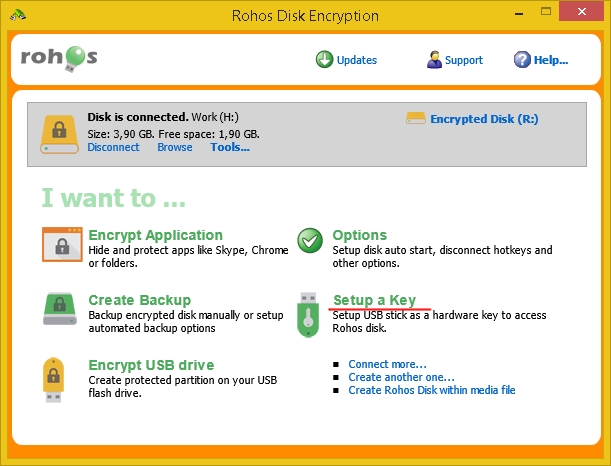
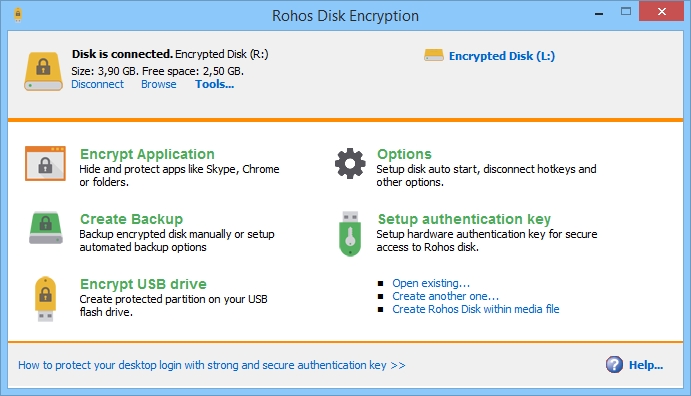
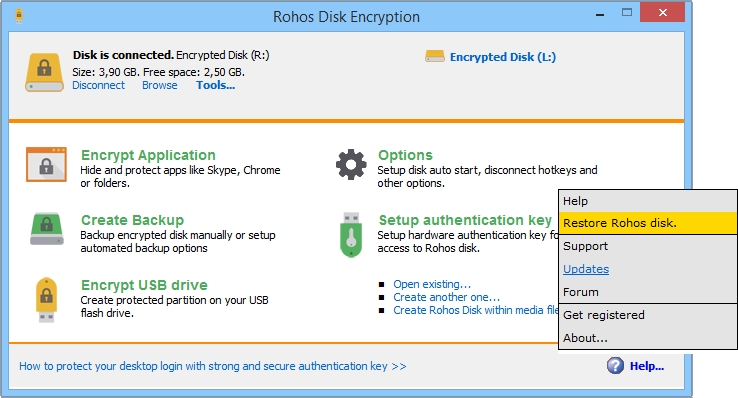
You can create a key using the setup wizard immediately after installation, or by using the Setup a Key command in the main program window (see the illustration).
The disk password is stored on the key in an encrypted format. When using several tokens, you should set and memorize a PIN code. All devices, with the exception of USB Flash storage devices, require that you install the manufacturer’s drivers. Some tokens or smart cards require that you initialize them first using the manufacturer’s utility. At our blog you will find an overview of the most popular tools for protecting your information.
Naturally, for decrypting a disk placed on a USB storage device, you cannot use the same USB storage device as an access key.
Open the program options. Here you can set automatic activation of the encrypted disk when a key is connected, as well as automatic deactivation of the disk when the key device is removed.
TIPS FOR USING AN ELECTRONIC KEY FOR PROTECTING YOUR INFORMATION
Over time, electronic keys have proven themselves as a useful and vital solution. They are strong and reliable tools for information security. Below we offer some tips that we feel are especially important:
- Keeping a spare copy of a key will make it much easier and faster to access your information in the event that the first key is lost or damaged. If you have decided to use electronic keys, then buy two of them, configure them both, and keep the second as a backup.
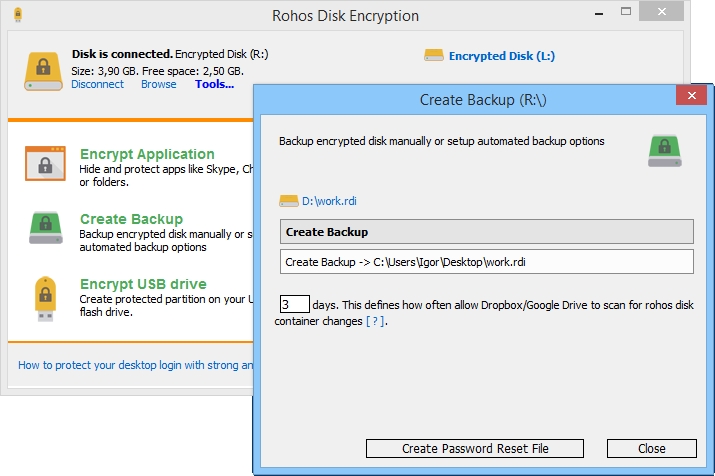
- If you do not wish to create a second copy of the key, then it is advised that you make a backup copy of the certificates and other key information located on the electronic key. This is also the best practice. Such backup copies must be kept in a secure place.
- If you own a laptop computer, then you should use a micro version of the key device. These do not greatly protrude from the laptop body and are not as susceptible to damage. Read our overview of ruToken micro keys.
- It is important to note that you do not have to worry about leaving the token connected to the laptop or desktop computer when you are away from it. Thanks to the PIN functionality, the electronic key is protected against use by a third party. No one can use the key without the PIN code, and in the event that the wrong PIN code is entered three times, the key is automatically blocked. A key can be unblocked using the Administrator PIN.
- By default, the Administrator PIN is set on all tokens and its value is shown in the documentation. Therefore, you must change it immediately to a new value. Changing the Administrator PIN can only be done using the token service utility provided by the manufacturer. Again, we recommend storing the new Administrator PIN in a safe place.
In Rohos Disk, there is a convenient function for disabling access to a Rohos disk when you are away from it. When you return, the Rohos program will ask for the token’s PIN code. The user will have 25 seconds to supply this information before the disk is automatically disabled for security reasons.
Screenshots:















 In short: now the popular ruToken identification device can be used in Rohos Logon Key and Rohos Disk as the one key needed to log in to Windows and your protected data. Rohos Logon Key works fully on Windows Vista/7 and also supports authorization for remote desktops using a ruToken. User authentication and identification with USB keys.
In short: now the popular ruToken identification device can be used in Rohos Logon Key and Rohos Disk as the one key needed to log in to Windows and your protected data. Rohos Logon Key works fully on Windows Vista/7 and also supports authorization for remote desktops using a ruToken. User authentication and identification with USB keys. Logging into Windows with ruToken.
Logging into Windows with ruToken.
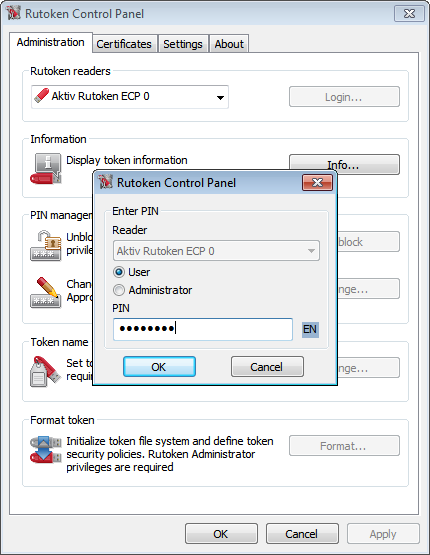









 Now the popular token ruToken can be used in Rohos Logon Key and Rohos Disk programs as a single Key for Windows (including Vista x86/x64) authentication, and for data protection on Rohos Disk.
Now the popular token ruToken can be used in Rohos Logon Key and Rohos Disk programs as a single Key for Windows (including Vista x86/x64) authentication, and for data protection on Rohos Disk.